Zero Trust Network Access – ZTNA
As the network perimeter evolves, technologies like Zero Trust Network Access (ZTNA)—a cloud-based service—enable us to provide access to internal applications only when needed. This approach prevents unauthorized access and lateral movement within the network, significantly reducing the company’s exposure to cyber threats.
Redefine the Perimeter (ZTNA)
Move away from traditional VPNs for network access. The ZTNA model provides granular access to applications, no matter where users are located. As a cloud-based service, it reduces the attack surface and improves the organization’s security posture.
-
- Restricts remote workers’ network access to only the applications they need.
- Integrates with SD-WAN or SASE solutions for comprehensive end-to-end coverage.
- Features easy deployment and configuration through a single console.
- Enables role-based access for each user and application within the ZTNA framework.
- Reduces access permissions if a user’s account is compromised.
ZTNA Market Overview
In recent years, the way employees interact with company resources has changed significantly. With the rise of remote work, traditional network perimeters have become less defined. Users now access corporate applications spread across both cloud environments and private data centers, resulting in new challenges and threats.
While many companies have relied on VPN solutions in the past, this approach proves inadequate for the current situation. VPNs simply aren’t scalable enough to meet the demands of today’s modern, digital, agile organizations and their users who require reliable access to data and applications from anywhere in the world. VPNs also create security issues due to an expanded attack surface and overly permissive network access. Furthermore, if a third party gains access to user credentials, the risks are severe. If this were to occur, the attacker could gain unrestricted access to the entire network.
To address these challenges, the industry is turning to ZTNA solutions, which offer granular access to applications or resources after users are authenticated and authorized. It also supports two-factor authentication and host-based controls to prevent credential theft. Once authenticated, ZTNA provides users with access to specific applications through a secure, encrypted tunnel to the cloud platform, offering an additional layer of security.
In this way, ZTNA access models operate much like software-defined perimeters (SDPs), relying on the “dark cloud” concept to prevent users from seeing applications or services they are not authorized to access. This also offers protection against lateral movement attacks; even if an attacker gained access to the network, they would not be able scan for other services.

What are the important points related to Zero Trust Network Access

Granular Access Control
Thanks to simplified management, applications can be registered either individually or in groups, while ZTNA policies provide granular access to internal company applications for designated users or groups.

Advanced Thread Protection (ATP)
Today, the volume of threats and malware targeting devices is on the rise. Teldat differentiates itself in the market by offering a Threat Prevention subscription alongside ZTNA. This combination enables us to detect suspicious behavior and known attacks against our applications and internal resources.

Scalable Performance
A dynamically scalable solution, like one hosted in the public cloud, adapts to the varying data demands and traffic within the office, offering significant benefits. A cloud-based ZTNA solution enhances scalability while Teldat’s approach ensures that instances are not shared among clients, providing exceptional isolation and resilience.

Access Verification
Access to the platform is managed through a specific agent, which is digitally signed by the user to prevent unauthorized access due to credential theft. This agent checks if the device complies with security policies and grants access to applications or resources based on the user’s access profile.
ZTNA Beyond IT Networks
The lack of a true security perimeter makes it difficult for companies and users to fully trust internal network connections. ZTNA solutions offer robust access control by limiting general access to resources and applying policies based on identity and context. Furthermore, ZTNA acts as an intermediary layer between users and the organization, enabling the implementation of additional security measures.
Zero Trust Network Access (ZTNA) streamlines application access by integrating private cloud, VPN, and SaaS into a unified approach. It provides centralized control, with the scalability and flexibility needed to offer users appropriate access based on their devices, location, and time of day.
When talking about centralized and unified control, we not only refer to users. Zero Trust Network Access (ZTNA) provides secure access for unsecured IoT devices, which have become increasingly common in networks (e.g., sensors, cameras, automation systems).

These devices often lack the robust security features of user equipment but still connect to the network. Additionally, they can be vulnerable if their firmware is not regularly updated. Therefore, it’s crucial to manage network access and control which applications these devices are allowed to access.
Integrating ZTNA with visibility tools like XDR can also strengthen security across OT and IT networks by detecting anomalous behavior, such as failed access attempts, unusual data transfers, or access at unusual times. In addition to monitoring activity, this combination also enables the tracking of device models and operating system versions for all connected devices.
Over time, Zero Trust Network Access (ZTNA) will become a key element of SASE services. These services integrate network and security functions at the client level, extending beyond individual users to provide a comprehensive security framework.

Teldat´s ZTNA Solutions & Products
The background
Not long ago, traditional security for IT and telecommunications relied primarily on antivirus software and firewalls. The outdated belief that anything within the security perimeter was trustworthy left companies highly exposed to cyberattacks. As software complexity and dependency increased, it became clear that new security solutions and layers were needed. Today, many attacks are launched from within the network itself.
Teldat’s ZTNA effectively manages compartmentalization and access control by implementing a “Default Deny” strategy. This isolates systems until a specified level of trust in confirmed, helping to secure information and mitigate damage in the event of credential compromise or infrastructure attacks. Furthermore, Teldat’s ZTNA technology creates a “dark cloud” perimeter, making it difficult for attackers to scan for vulnerabilities, unlike traditional VPNs.
Furthermore, Teldat’s ZTNA technology creates a “dark cloud” perimeter, making it difficult for attackers to scan for vulnerabilities, unlike traditional VPNs.
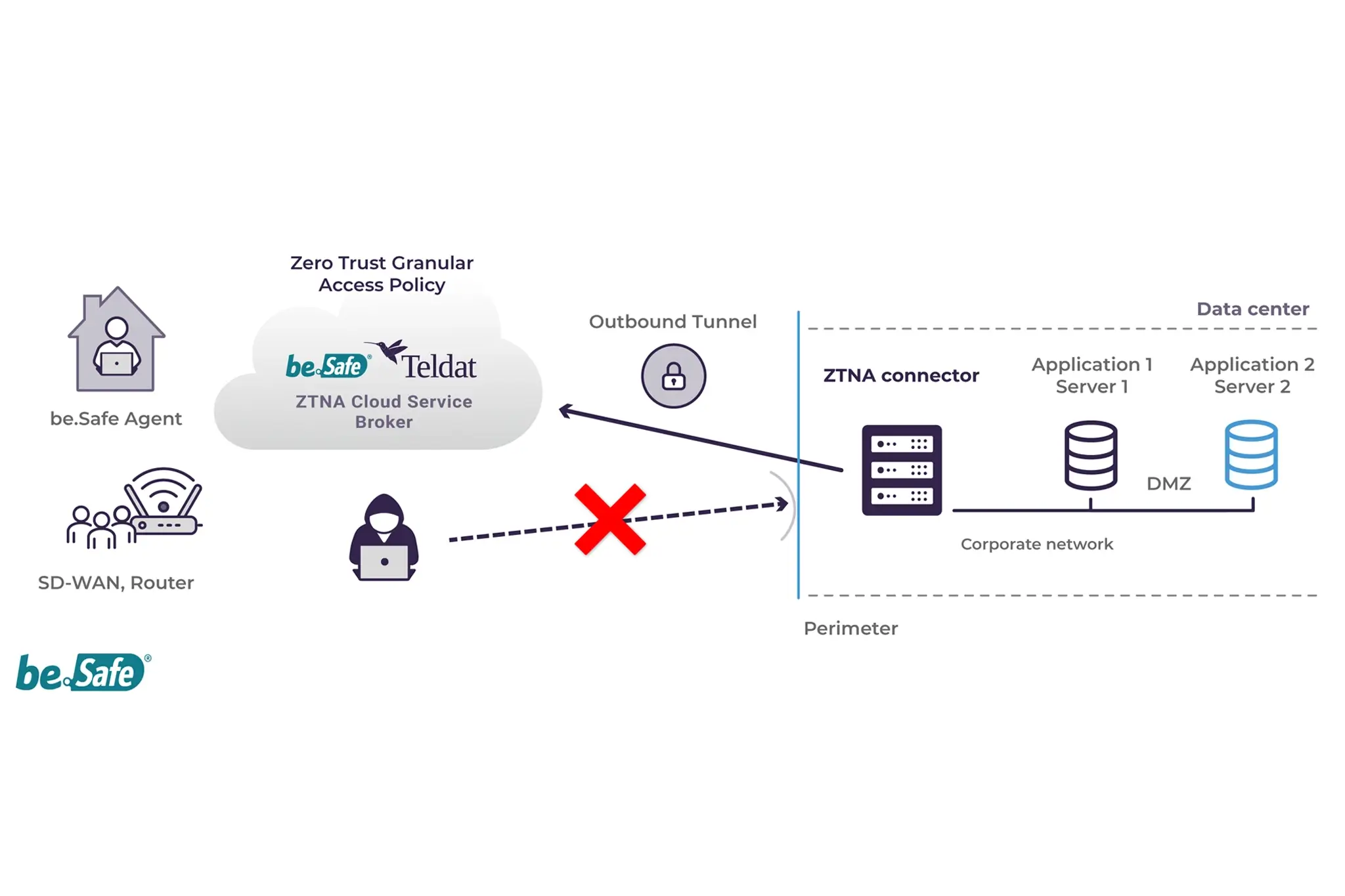
be.Safe Pro – ZTNA Architecture
Teldat’s be.Safe Pro security solution is tailored for corporate and SMB clients. It features three key components: an agent installed on each device, a cloud-based Broker that manages connections and enforces granular access policies, and a connector that can be deployed as a virtual image of our operating system in the area where internal applications are accessed. The connector establishes a secure tunnel to the cloud Broker while also allowing for the implementation of local control policies.
be.Safe Pro provides centralized management via a single cloud-based console, facilitating all configuration tasks. This includes provisioning users and installing their agents, synchronizing permissions with the directory, registering internal applications and DNS, and deploying various connectors to link users and applications across the platform. Multiple connectors can be used as needed, accommodating internal applications located in various network segments or in the cloud.
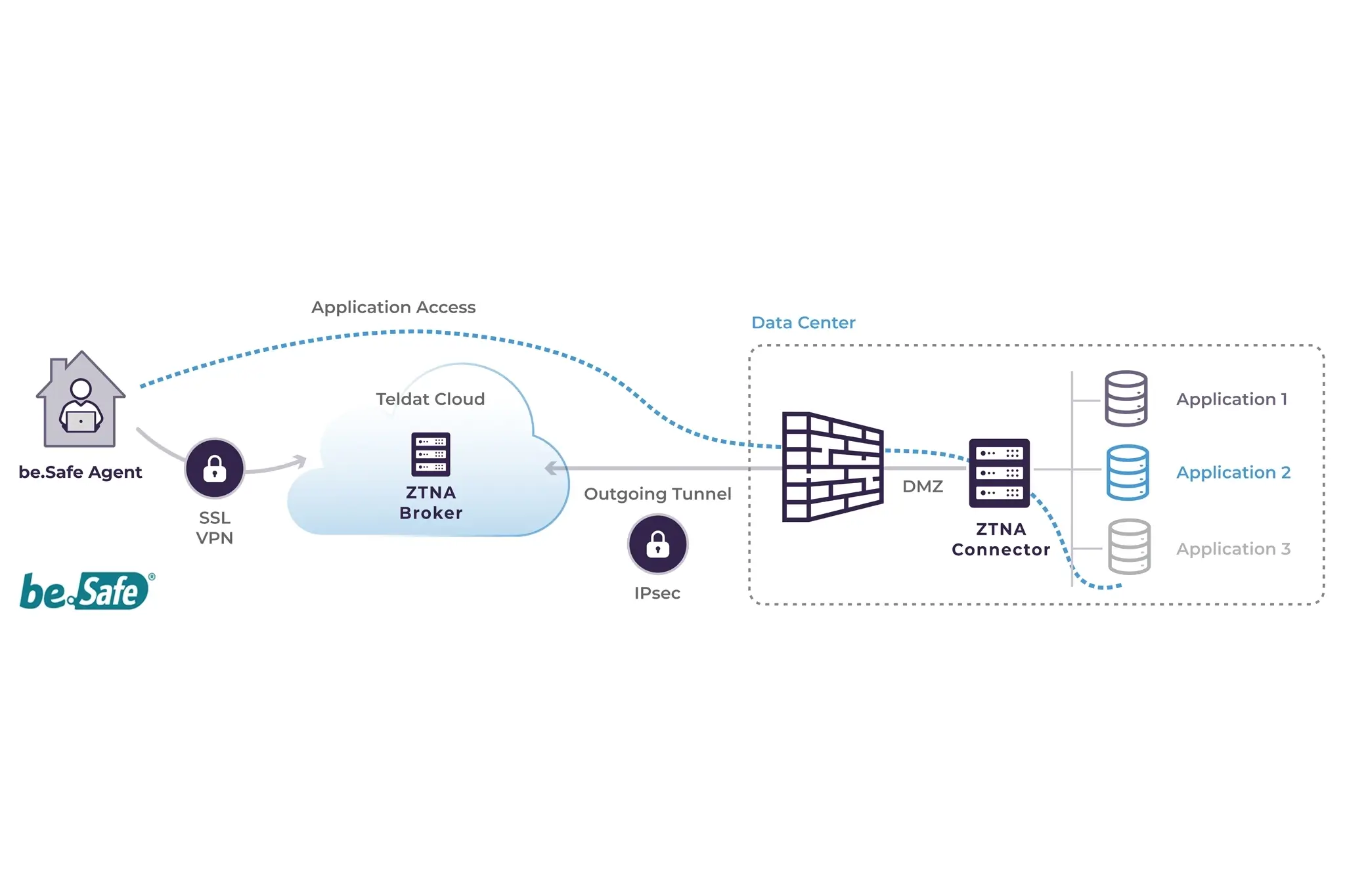
Advanced Policies
After deploying the components and provisioning users with their agents, applications need to be registered by Host, URL, IP, and port. This, along with authorization settings from the directory, allows for the creation of detailed access policies tailored to individual user profiles.
With Teldat’s be.Safe Pro, administrators can easily implement additional security features, such as threat prevention profiles for any traffic passing through the platform. It also enhances and controls user internet access by routing it through the platform and applying features like URL filtering and application control.
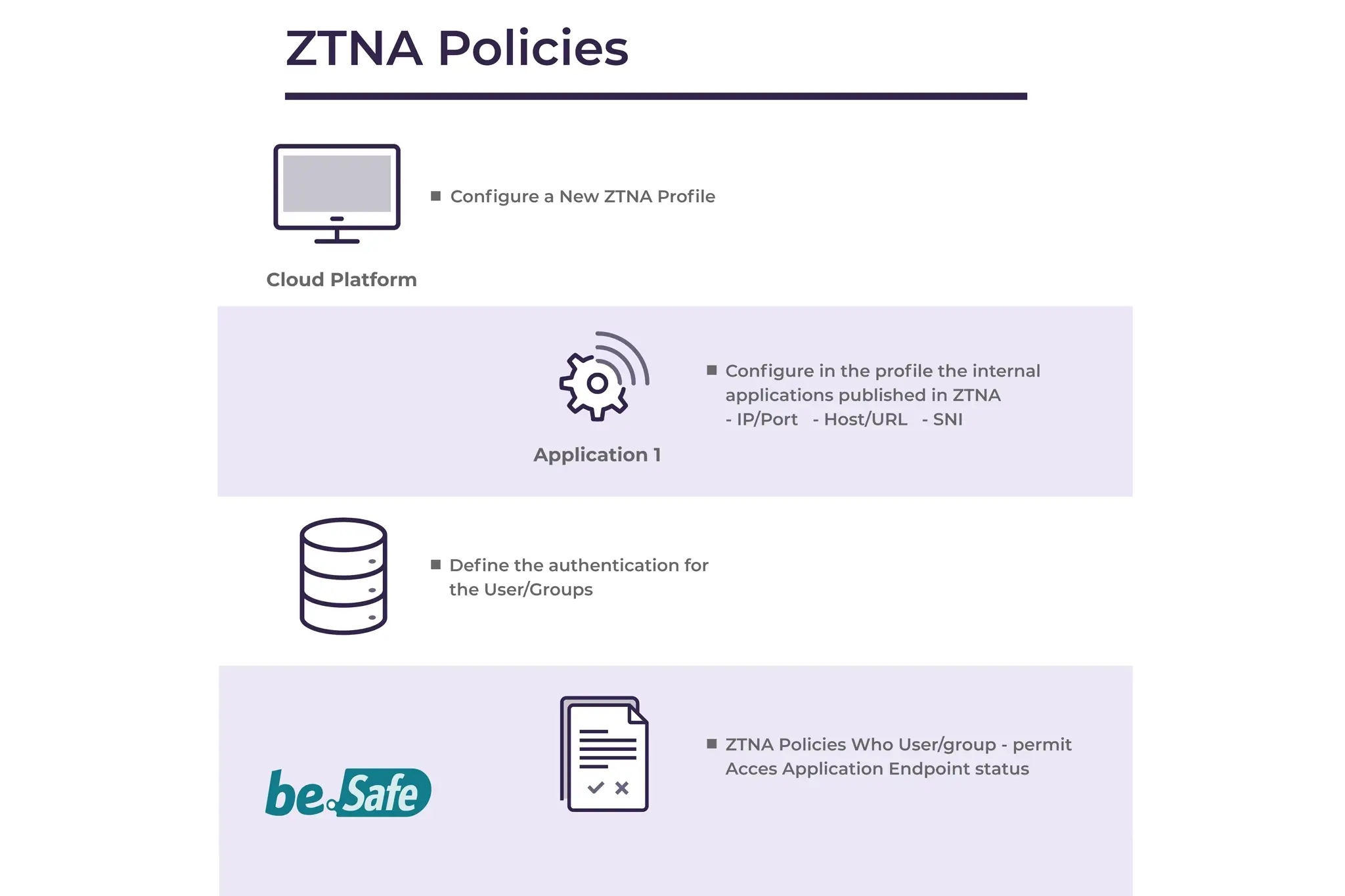
ZTNA Features
Teldat provides a unique solution for IoT devices, allowing access from remote physical devices that establish a tunnel to the service without needing an installed agent. This method is ideal for managing IoT devices connecting to the network, enabling the identification of their origin and the implementation of visibility and control policies.
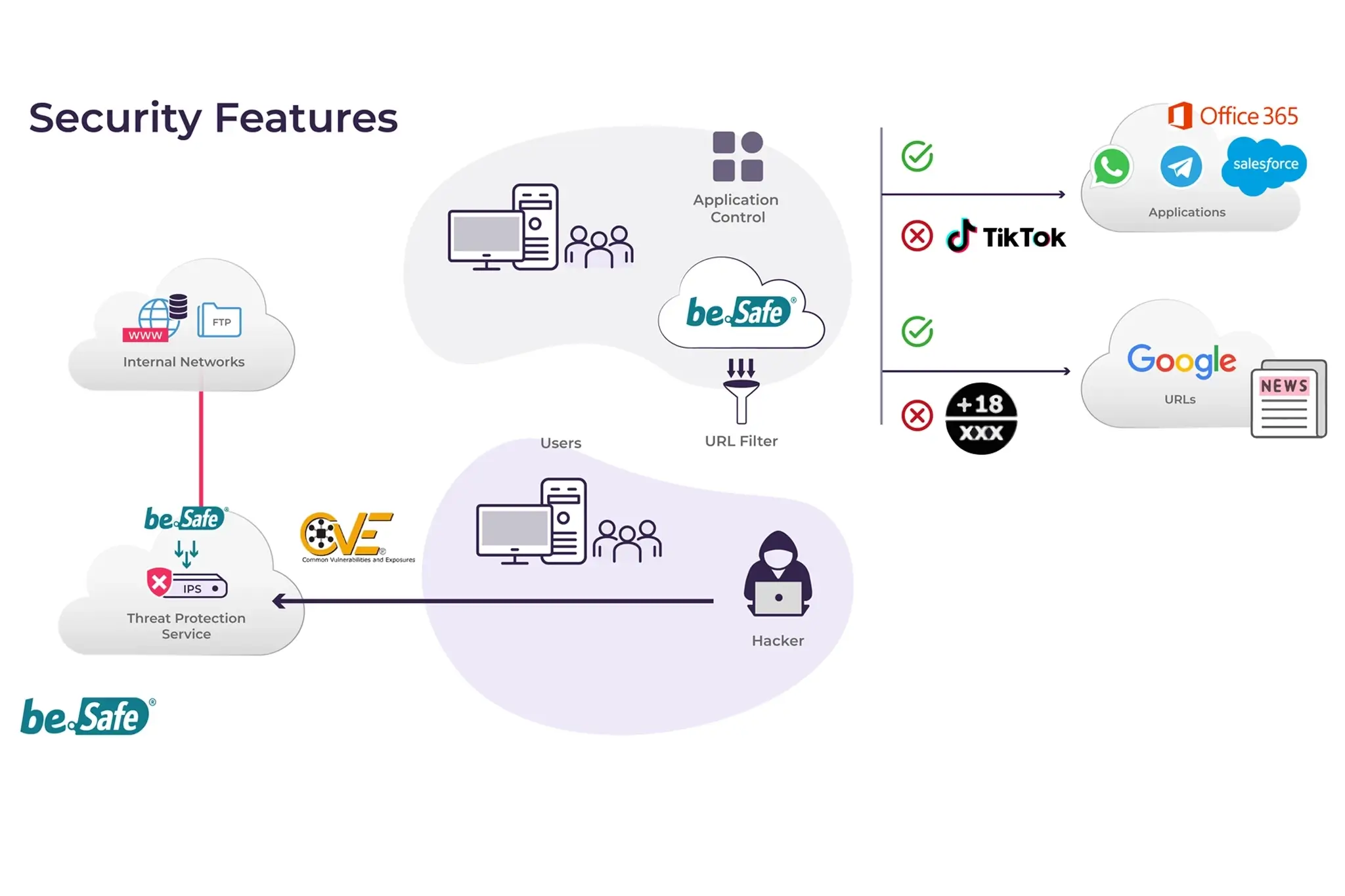
Teldat´s ZTNA Use Cases
SMB evolving to cloud environments
Small and midsized businesses migrating their applications and servers to the cloud.
Increase control and visibility
Financial institutions use MPLS and VPN connections to access corporate servers to increase access control and obtain more information.
SMB evolving to cloud environments
Small and midsized businesses migrating their applications and servers to the cloud.
Challenge
Small and medium-sized companies usually use internal applications with servers hosted at a single site or in a shared physical data center, thereby allowing little flexibility of movement in an ever-changing environment where mobility is becoming increasingly important. Cloud environments provide an opportunity to locate applications anywhere in the world, which gives a lot of flexibility but also widens the security perimeter as all connections from public Wi-Fi environments or Internet access from non-business locations (for instance from home or from hotels and business fairs) need to be secured.
Solution

Teldat’s security solutions make it possible to remotely connect users from both offices and locations outside the client’s network, applying customized access policies for each user or group of users.
In this way, access confidentiality is ensured, and only necessary permissions are granted, complying with the premise of “Zero-trust” instead of any logged-in user having all possible privileges.
Why Teldat?
Teldat offers various robust and versatile security solutions, with intuitive interfaces to allow any user to easily manage their own policies and connections. Furthermore, the HW-agnostic technology supports connections from all devices complying with tunneling standards, irrespective of manufacturer.
Increase control and visibility
Financial institutions use MPLS and VPN connections to access corporate servers to increase access control and obtain more information
Challenge
By using MPLS connections from branch offices and VPN clients for remote workers, the bank is unable to grant granular access permissions to applications according to user or device type. It also lacks a visualization tool to show how each user is using the network and resources, or how these are being accessed, thus the sizing of network access and server capacity is a difficult task for the IT team.
Solution

With Teldat’s security solutions, it is possible to control access to all corporate applications and access to the Internet and SaaS platforms in a personalized and granular way thanks to their integration with active directory and SSO tools. Both access from branch offices and access from remote connections can be controlled.
In addition, Teldat’s visibility solutions provide all the information necessary to understand how resources are accessed and by whom, so that the bank can obtain information on possible attempts to violate rules by devices that may have been hacked.
Why Teldat?
Teldat’s be.Safe and be.Safe XDR solutions offer secure and reliable access with intuitive interfaces to allow users to easily manage their own policies and connections, and customizable dashboards to display information graphically. They are also HW agnostic, so any device complying with tunneling and flow information sending standards, irrespective of manufacturer, can connect.
Segmenting access to internal networks
Compartmentalize networks by granting permissions according to role and device type.
Challenge
Legacy network configuration greatly complicates the task of segmenting internal networks for controlling user and device access to company resources. On the one hand, there may be certain departments that shouldn’t have access to other departments’ resources, only to those assigned to them. On the other hand, a security breach in a device on a specific network could end up infecting the rest of the departments through the sideways movement of information – imagine a laptop that has been infected via a USB device or a tablet that has downloaded a malicious file.
Solution
Thanks to SW-defined networking solutions and security platforms, each network can be completely isolated from the others and the access to each controlled according the user or specific device.
Graphical interfaces are used to apply independent policies for both traffic to the datacenter and SaaS applications, and to deny access to unauthorized resources. Likewise, as the networks are compartmentalized, when a virus is detected in a device, it can be contained within the environment where the device is located instead of jeopardizing the rest of the company’s networks or central servers.
Why Teldat?
Teldat’s be.SDWAN and be.Safe solutions offer segmented and compartmentalized access with intuitive interfaces so users can easily manage their own networks and security policies.
Read our latest Blog Posts
Post-Quantum Cryptography: The Future of Digital Security
Cryptography is the backbone of modern digital security, protecting everything from banking transactions to personal communications. However, advances in quantum computing threaten to break many of today’s cryptographic systems. This has spurred the development of...
Threats to Cybersecurity in the Banking Sector
The digitalization of the financial sector has optimized service efficiency, remote access to banks and improved user experience. However, the risk of suffering cyberattacks has grown exponentially. In this context, cybersecurity has become a key strategic pillar for...
AI Under Attack: A Threat Evolving at the Speed of Technological Innovation
In 2025, Artificial Intelligence (AI) systems are not only tools for productivity, automation, and advanced analytics—they have also become new attack vectors for cybercriminals. From data manipulation to direct model exploitation, the threat landscape is evolving as...