be.Safe XDR
Network Traffic Analysis tool
Regain visibility and control of your Cloud-based physical and virtual networks
Network Traffic Analysis

As IT moves into the Cloud for delivery as a service, organizations lose visibility of their network infrastructure. be.Safe XDR Network Traffic Analysis tool (NTA) gives users back control and informs their strategic decisions.
-
- be.Safe XDR´s business-type vocabulary is easily understood by all users profiles
- Scalable and suitable for organizations of any size and complexity
- Uses telemetry from all network manufacturers’ equipment
- Troubleshoots network performance and curbs malware
- Monitors user behavior and controls shadow IT
Network traffic analysis tools market overview

The client was already aware of Teldat’s expertise in the world of IP networks and cellular interconnections after working with Teldat on previous projects in other parts of the world.
Similarly, the client had already experienced the high-quality service and technical support provided by Teldat.
Teldat has been in the telecommunications sector for more than 40 years and is a benchmark in terms of quality solutions. Its ability to offer a holistic hardware/software solution covering Wi-Fi connectivity and cybersecurity also made Teldat the perfect partner for this project.
These factors present network administrators with a dynamic environment, owing to the rising volume of system applications, increasing numbers of mobile end devices that are often employee-owned (BYOD), and amount of transferred data in corporate and WAN networks. Data rates can reach ten gigabits, with distributed infrastructure, virtualizations, and cloud services. These trends have created a huge demand for stability and improved network administration.
The global network traffic analysis solutions market is growing through meeting this demand with tools for high transparency communication at both system and device levels and requirement, and control over applications. Such solutions aid in maintaining high network security, reduce the time needed to resolve network issues, and monitor user behavior and network capacity consumption, while pre-empting problems relating to networks and applications.
What are the important points related to Network Traffic Analysis tools?

Provides broad views of network activity
Popular Network Traffic Analysis solutions delivers the essential information needed to impose control and take any necessary strategic decisions: these permit operators to optimize their existing infrastructure with confidence.

Network Traffic Analysis integrates a variety of technologies
Network Traffic Analysis solutions collect real time data, and enrich it to provide insights. Query systems operate to the required granularity, and data is unified for interoperability. Network Traffic Analysis uses machine learning to learn network behavior and find anomalies.

Network Traffic Analysis gives access to every network aspect
Network Traffic Analysis reveals user behavior, detects bottlenecks, and makes troubleshooting easy. It allows forensic analysis, builds business vision and infrastructure optimization. Users can take actions based on facts.

Network Traffic Analysis tool promotes reliable network management
Network Traffic Analysis provides a powerful, flexible, simple, and visual tool to generate and reveal relevant information as it is needed. With the correct network information, network operations teams can manage their network reliably.
Understanding Network Traffic Analysis
A well-performing network is critically important to digital business; however, its visibility and users’ understanding of it often don’t meet operational requirements.
IT is no longer contained within a controlled internal environment. Infrastructure is moving steadily out of the office, being consumed instead as a service. Yet the equipment that inevitably remains on site comprises many devices from different manufacturers that cannot easily be monitored.
That’s why Network Traffic Analysis (NTA) solutions are increasingly popular: they provide a much broader view of their network’s activity without calling for assumptions.
They deliver the essential information needed to impose control and make strategic decisions that allow users to optimize their existing infrastructure with confidence.
Network Traffic Analysis (NTA) is easy to implement, and lets users
- Take action based on facts.
- Optimize infrastructure.
- Detect bottlenecks.
- Gain business vision.
- Troubleshoot easily.
- Perform forensic analysis.
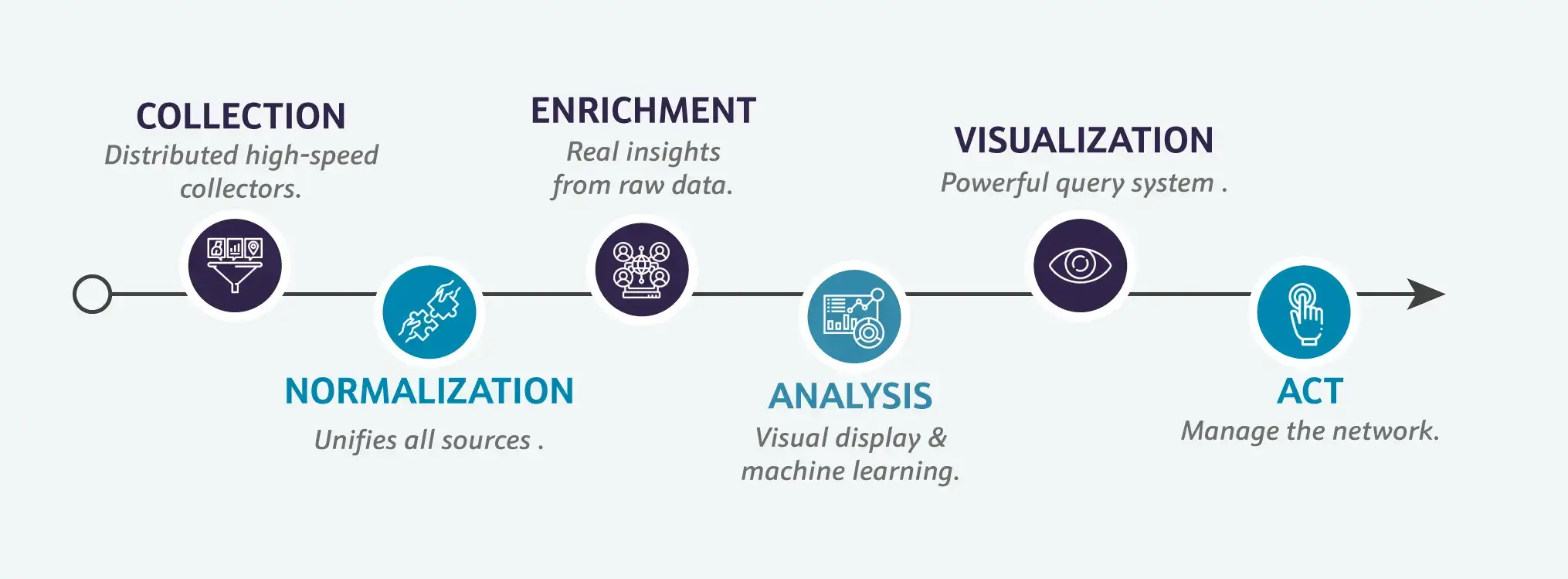
Network Traffic Analysis technology (NTA) comprises six parts:
Collection: Distributed high-speed collectors digest the telemetric and flow data coming from the network devices at real-time speed.
Normalization: No matter the origin of the network event, the normalization process unifies all sources into standard system dimensions to allow interoperability
Enrichment: Using third party and internal intelligence feeds, the platform enriches every event to provide real insights derived from the raw data
Analysis: Through machine learning techniques, the platform learns the network behaviors and discovers anomalies
Visualization: A powerful query system will interrogate any aspect of the network performance, usage, KPIs or relevant security information at the granularity level required.
ACT: With the correct network information, network operations teams can reliably manage the network.
be.Safe XDR Solution & Teldat Products
The background
All companies increasingly depend on third-party service solutions. This means they are unable to check or monitor for themselves whether their contracted services meet their SLA or are performing well. They may suspect they are not fully benefiting from their network, or are paying for under-utilized infrastructure – but cannot be sure.
be.Safe XDR is the perfect answer: It is a next-generation NTA (Network Traffic Analysis) platform that gives users the increasingly critical ability to view their network’s status and control it accordingly. This view is in-depth, detailed, unbiased, and user-controlled, while being compatible with any network vendor.

be.Safe XDR – a tool for everyone
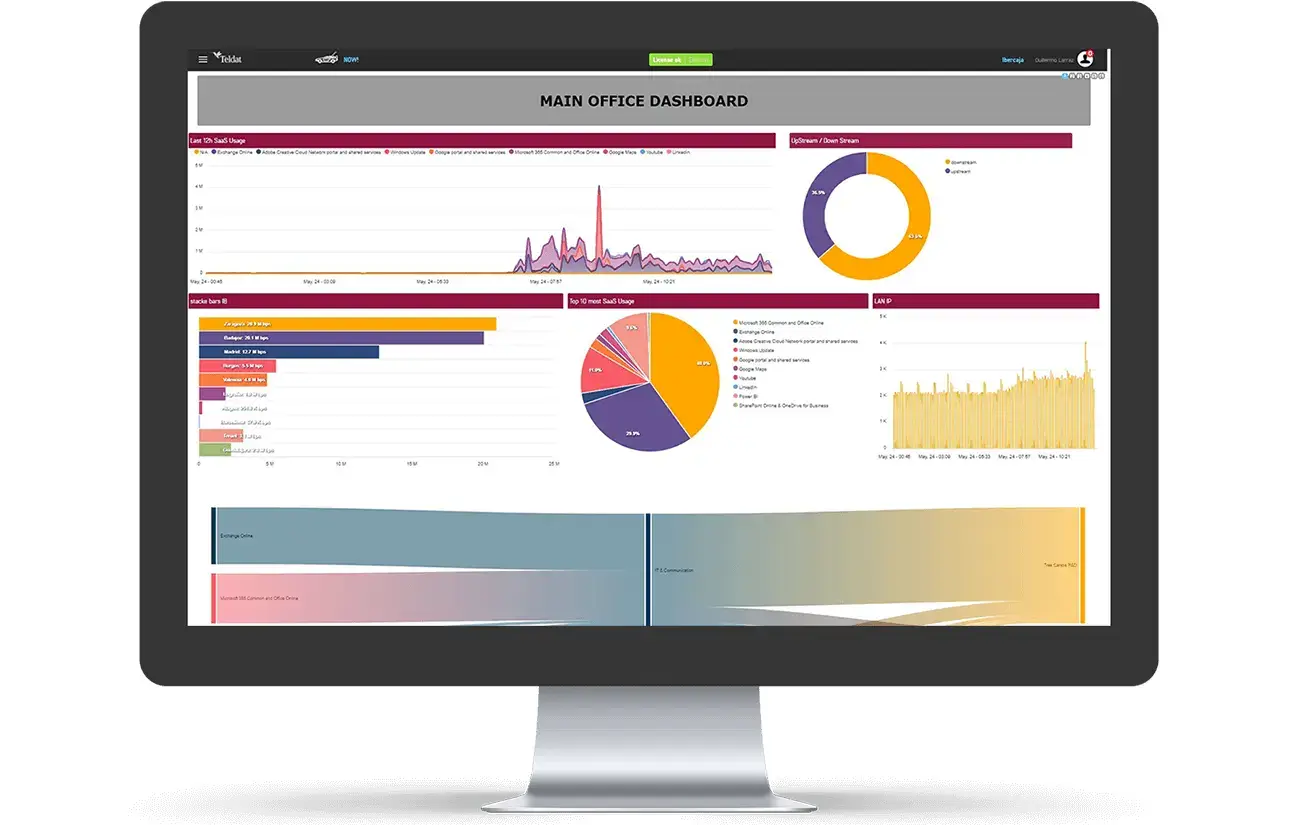
Critically, be.Safe XDR is far from just a technical tool for the IT and Communications departments. It brings immediate, actionable information to the entire enterprise, through its business-oriented vocabulary and user-friendly interface. The CEO or anyone else in the company, even without technical knowledge, can consult and understand be.Safe XDR
be.Safe XDR provides an interactive, agile, and powerful tool for real-time and historical network data. Users can freely design unlimited Dashboards and Reports, and can also configure alarms for network situations requiring attention.
be.Safe XDR – Adaptable & Scalable
Provided as a service from the cloud (SaaS) for monitoring and diagnosis, and analysis of both physical and virtual networks in environments from any network manufacturer, it uses the telemetry that these networks produce.
be.Safe XDR´s hierarchical, multi-tenant and multi-tiered architecture makes it ideal for organizations of any size and complexity. With its powerful Big Data structure, the architecture can scale for large infrastructures and respond to NPMD (Network Performance Monitoring and Diagnosis) challenges for service providers, managed service providers, large companies, or small and medium organizations with specific network visibility needs.

be.Safe XDR’s Network Monitoring & Management
Correct and appropriate network use: Are all users using the latest approved applications, and nothing incompatible with their department’s role? Is any device accessing an unauthorized resource? Monitor how users are accessing applications, to control shadow IT and ensure only trusted, allowed applications are being used.
Network sizing and futureproofing: Find out if your infrastructure is optimally sized, and anticipate capacity needs for new applications. Analyze network trends and forecast investment based on traffic, growth rates, interface capacity and runout dates.
Curb malware impact: Get an overview of locations affected by malicious activity, classify malware types, and analyze time periods where malicious traffic was detected for each location individually
Network performance: Detect network or local outages for fast troubleshooting, and monitor business-critical applications’ performance. be.Safe XDR also makes patterns and anomalies visible.
Use cases
Cloudbased tax collection administration
How tax authorities are improving their collection services with cloud technology
Challenge
Cloud technology is offering tax authorities an opportunity to improve the tax experience for themselves and their users. By digitizing tax, tax authorities, accountants, and taxpayers can exchange tax information via cloud-based applications rather than paper records or spreadsheets.
Applying this digital transformation will reduce IT downtime for internal and external services, maintain daily IT service standards, and deliver IT projects on-time and to quality standards.
Network Traffic Analysis tools like be.Safe XDR can provide effective solutions to tax offices seeking to meet these commitments.
Solution

Tax authority organizations are large and complex – yet be.Safe XDR can help. It allows configurations for all organizations of any complexity. Users and devices (physical and virtual) can be nested in an organizational/regional hierarchy that best reflects their reality. Information can be freely filtered and analyzed into multilevel hierarchies. Dashboards and reports can be configured to show a specific view of the hierarchy or by arbitrary labels.
be.Safe XDR performance analysis also provides comprehensive information for users to detect bottlenecks. Results can be filtered by branch, department, or user to better understand traffic behavior and increase knowledge about application usage.
Why Teldat?
be.Safe XDR allows a multivendor environment, with collection and analysis of streams from devices like Teldat and many other leading vendors.
Its business-oriented interface means that all users, not just technical specialists, can easily obtain the information they need.
Multisite supermarkets retail networking
Supermarket chains with high store counts and large, complex data networks require powerful network management tools
Challenge
A large supermarket chain will comprise at least one corporate headquarters, several distribution centers, and hundreds of retail stores. Fast, reliable communications across such large, distributed, and complex estates are essential, for activities like managing web-based purchases, transferring stock between stores, and customer loyalty schemes. Stores’ sales data must be available to headquarters for stock control, insights, and analysis.
Users must not only manage retail tasks like optimizing large numbers of remotely deployed lines, but also administer the network itself, through applying rules across all the branches. Equally, they must check user behavior, ensuring that each department only runs applications suitable to their role.
Solution

Users can create Dashboards and share them with colleagues, in editing or view-only mode, add widgets based on analytics, and generate KPIs enriched with text, images or external websites. Complement all this with an editing capability up to six layers deep. Stay current with periodic refresh options, with opportunities of exporting reports.
be.Safe XDR provides a complete view of office status, from link quality to employee productivity. It enriches data in real time, showing who, when and where all devices are connected, recognizing security-critical connections like phishing or spyware, and non-productive applications like social networks.
Why Teldat?
be.Safe XDR can collect and analyze streams from Teldat and multipleother leading vendors’ devices. It can process traffic flows in all major protocols.
be.Safe XDR is not just easy to deploy, but also easy to use. Its business-oriented vocabulary is informative to all users, not just technicians.
Read our latest Blog Posts
Post-Quantum Cryptography: The Future of Digital Security
Cryptography is the backbone of modern digital security, protecting everything from banking transactions to personal communications. However, advances in quantum computing threaten to break many of today’s cryptographic systems. This has spurred the development of...
Your Features are only as Strong as Your Hardware
In the telecom world innovation has taken the spotlight, opening the doors to new protocols, cutting-edge features, ambitious capabilities like 5G, NGFW, etc. Yet behind the scenes, there's a less glamorous, but equally vital actor: the robust hardware supporting all...
Threats to Cybersecurity in the Banking Sector
The digitalization of the financial sector has optimized service efficiency, remote access to banks and improved user experience. However, the risk of suffering cyberattacks has grown exponentially. In this context, cybersecurity has become a key strategic pillar for...