Teldat Training
Customized training courses tailored to the needs of each client.
On-Line Certification
Integra-T offers on-line certification, covering all technologies marketed by our company.
At Teldat, we have an on-line training platform available to meet the training needs of all Teldat router users. The platform covers the following requirements:
-
- On-line classes to provide tuition on the contents designed for each certificate.
- Documents and manuals to help participants during the course.
Practical sessions, to complement training. - Attendee evaluation.
- Creation of Certificates.
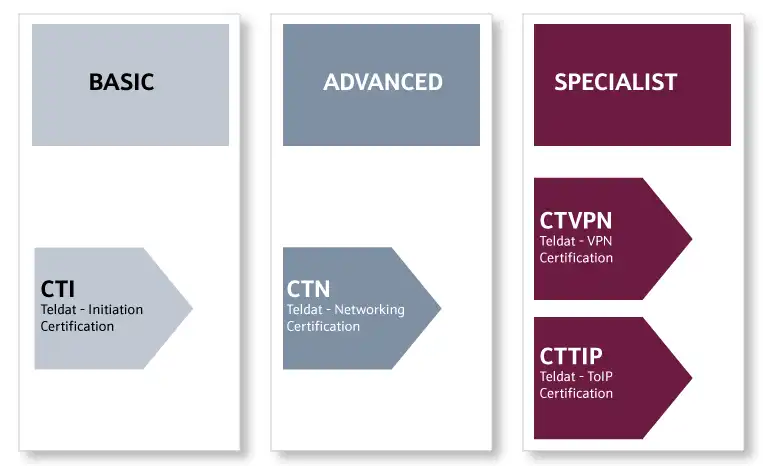
Teldat’s on-line certification offers training on all technologies marketed by the company and is structured and divided into several levels:
Our certification courses fall within the Integra-T Training Program, and are broken down as follows:
Basic
Certification for company personnel at level 1 (basic). At this level, our participants will acquire basic knowledge on how to handle any product that runs CIT (Teldat‘s Internetworking Code). This part will also include training on how to install Teldat products.
Advanced
At this level, our participants are instructed on Teldat Internetworking routers at an advanced level. This is the Certification for company personnel at level 2. This part includes configuring, monitoring and troubleshooting for basic internetworking scenarios.
Specialist
At this level, our participants specialize in handling network architectures based on Teldat technology and, more specifically, on how to generate Virtual Private Networks (VPN) and VoIP.
Trainning Plan
The certification courses fall within the Integra-T Training Program, and are broken down as follows:
Length of courses
The courses last for a maximum of 3 months per certificate.
Methodology
Participants must be pre-validated in the platform in order to register in one of the on-line certified training courses.
Please follow these steps to register for one of Teldat’s online training courses:
-
- Click on the URL: https://training.teldat.com/online/ and register for a training course.
- Once registered, a window containing two tests will appear: select and complete the appropriate test.
- The system will check you are registered as user in the application. If validated, you will be registered in the appropriate certification course. If validation does not complete, the system waits for you to be validated.
- Once accepted on a certification level, you must complete it.
- At the end of the course, you are required to take two exams: practical and theoretical.
- If you pass, you will be given certification for the level obtained.
Any doubts, questions or issues regarding our on-line training should be sent to our support team at the following address:
CTI Certification
Aims
Teldat devices: Installation.
-
- To display the characteristics of all the TELDAT Router families.
- To select the most appropriate equipment for each kind of network.
- Install a router, assembly and the different kinds of verifications for configuration.
- Demonstrate the recovery procedures for the devices.
Configuration, management and administration of networks with Teldat devices.
-
- Know how to solve problems derived from the configuration.
- Basic troubleshooting, general device monitoring and how to activate the events.
- To know all the configuration and administration procedures for the routers.
Contents
Module 1. Internetworking: Basic knowledge.
-
-
- OSI Layers.
- Types of protocols.
- TCP/IP stack.
- IP and Mask addresses.
- Types of routes.
-
Module 2. Installation.
- Licensing system.
- Connectors.
- Device LEDs.
- Default configuration.
- Smart-card.
- Drivers.
- Rack installation.
Module 3. BIOS Menu.
- CIT.
- BIOS menu.
- BIOS operations
Module 4. Upgrading the Software.
- Distribution file.
- Upgrading the software.
Module 5. Administration.
-
-
- Accessing the device.
- Configuration.
- Monitoring.
- Events logging system.
-
CTN Certification
Aims
Interfaces
- The TELDAT router interfaces can be configured at the physical layer without the need for an associated protocol or an encapsulator. This unit provides information on what interfaces the routers support (physical, virtual and semi-virtual) and how to configure and monitor them.
- Protocols: This unit focuses on how to configure IP (and protocols associated to the IP world), debugging and functions. Once completed, the next phase concentrates on routing protocols.
- Encapsulation: This focuses on assembling a series of mock-ups and the various ways to encapsulate said module
- Features: This final unit concentrates on features, such as Sniffer debugging: features to improve Backup (WRR), improve performance (DHCP or VRF), traffic prioritization (QoS) and security (AFS).
Contents
Module 1: Basic concepts
Module 2: Introducing Interfaces
Module 3: LAN Interfaces (with VLAN tagging)
- LAN motherboard
- Switch
- Bridge
- Module 4: Interfaces xDSL1
- ADSL Interface
- Subinterface
- Introducing PPP
- SHSDL
- VDSL
- Encapsulators:
- IPoATM
- PPPoATM
- PPPoEoATM
- BridgeoATM
Module 5: Cellular Interfaces
- 3G
- LTE
Module 6: Serial Interfaces
- Synchronous/Asynchronous
- HDLC
- SDLC
- PPP
- MPPP
- FRL
- X.25
- Scada
Module 7: G703 Interface
- Introduction
- PPP/MPPP
- FRL
- HDLC
Module 8: Wi-Fi Interface
- Router acting as Access Point.
- Router as client.
Module 9: Loopback Interface
Module 10: IP/routing
- IP Configuration
- ACLs
- Policy Based Routing
- Static Routing.
- RIP & filtering.
- BGP & filtering
- OSPF & filtering
- PIM-SM
- Intelligent Routing (with IP SLAs):
- NSM
- NSLA
- Application
Module 11. Features
- DHCP
- Client
- Relay
- Server
- NAT
- Traditional
- New NAT(AFS)
- Static
- Dynamic
- OverloadNAPT
- WRR
- VRRP/TVRP
- DNS
- NTP
- GPS
- SNIFFER
Module 12. QoS
- Introduction
- Type of QoS
- Advanced parameter
Module 13. Manager
-
-
- SNMP
- Syslog
- Netflow
-
CTTIP Certification
CTVPN Certification
Read our latest Blog Posts
Post-Quantum Cryptography: The Future of Digital Security
Cryptography is the backbone of modern digital security, protecting everything from banking transactions to personal communications. However, advances in quantum computing threaten to break many of today’s cryptographic systems. This has spurred...
Constraint-Based Electronic Design
"The Constraints". While electronic schematics provide a practical way to represent the components and connections within a circuit, they are ultimately a simplification that overlooks important aspects of how the circuit actually behaves....
Your Features are only as Strong as Your Hardware
In the telecom world innovation has taken the spotlight, opening the doors to new protocols, cutting-edge features, ambitious capabilities like 5G, NGFW, etc. Yet behind the scenes, there's a less glamorous, but equally vital actor: the robust...

























