In today’s enterprise landscape, network security has become a top priority. As cyber threats grow increasingly sophisticated, it is crucial to ensure that only authorized devices and users can access the network. This is where 802.1X authentication, combined with Network Access Control (NAC) technologies, becomes indispensable. This article delves into how deploying 802.1X on switches significantly bolsters network security by authenticating and authorizing devices before they gain access, thereby safeguarding the organization’s critical assets.
In today’s enterprise landscape, network security has become a top priority. As cyber threats grow increasingly sophisticated, it is crucial to ensure that only authorized devices and users can access the network. This is where 802.1X authentication, combined with Network Access Control (NAC) technologies, becomes indispensable. This article delves into how deploying 802.1X on switches significantly bolsters network security by authenticating and authorizing devices before they gain access, thereby safeguarding the organization’s critical assets.
The Security Challenge of Switches
Switches are critical elements of network infrastructure, serving as key connection points for all network traffic. Without robust security measures, these devices can become vulnerable entry points for unauthorized access and malicious activity. While traditional security methods, such as Access Control Lists (ACLs) and VLAN segmentation, have been effective, they fall short of meeting today’s complex challenges. This is where 802.1X authentication and NAC come into play, offering a more proactive and robust approach to network protection.
Implementing 802.1X on Switches with NAC
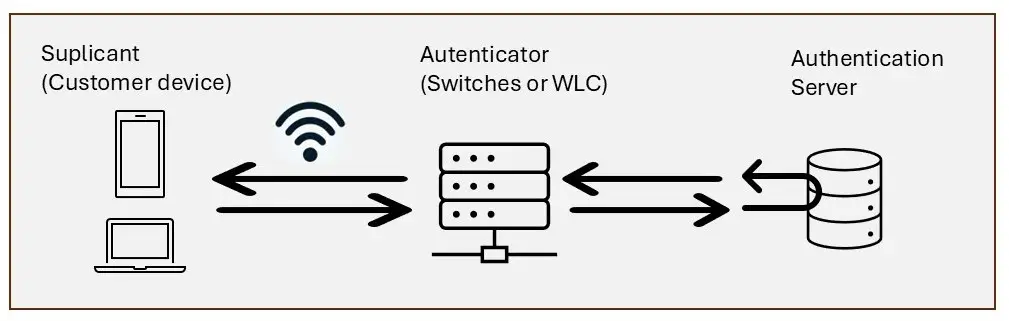
The Extensible Authentication protocol (EAP) is used to authenticate devices on the network before they are granted access. This authentication occurs at the switch port level, ensuring that any device attempting to connect must first be verified through the switch, which functions as a network access controller (NAC).
How 802.1X Works
1 – Connection Request: When a device attempts to connect to a switch port, the port stays in an unauthorized state until authentication is successfully completed.
2 – Authentication Initiation: The switch, serving as the authenticator, sends an authentication request to the device trying to connect. The device then responds with its credentials (such as a username and password, or a digital certificate). This initial exchange is crucial for establishing a secure and controlled connection.
3 – Credential Transmission: The credentials are sent to the authenticator, which is the switch in this case, and then forwarded to the authentication server (typically a RADIUS server) for verification. This process ensures that the credentials are evaluated centrally and adhere to stringent security standards.
4 – Verification and Authorization: The authentication server checks the credentials, and if they are valid, authorizes the switch to grant network access to the device. If authentication fails, access is denied. This step is essential for maintaining network integrity and security, ensuring that only authorized users and devices gain access.
5 – Policy Assignment: After authentication, the switch can enforce specific policies for each device such as assigning it to a particular VLAN, applying dynamic ACLs, or prioritizing traffic. This ensures efficient and customized management of network traffic.
Key Benefits of 802.1X with NAC
A) Enhanced Security: By requiring authentication for each device, 802.1X ensures that only authorized users and devices can access the network. This significantly reduces the risk of unauthorized access, creating a more secure and reliable network environment.
B) Granular Control: Identity-based policies enable administrators to enforce detailed access controls, ensuring each user or device has the appropriate level of access. This level of customization improves network management and reduces the risks associated with unauthorized access.
C) Full Visibility: Integrating 802.1X with NAC solutions provides network administrators with complete visibility into who is connected to the network, allowing for better management and incident response. This visibility is crucial for maintaining constant and proactive control over the network infrastructure.
Conclusion on 802.1X on Switches with NAC
In today’s digital landscape, network security remains an ongoing challenge. Implementing 802.1X on switches, complemented by a robust NAC system, is one of the most effective strategies for safeguarding enterprise networks. This approach guarantees that only authorized devices and users gain access to network resources, providing an additional layer of defense against both internal and external threats.
Teldat’s switching solutions are designed to seamlessly integrate technologies such as 802.1X and NAC systems, delivering a robust security layer that ensures only authorized users and devices can access the network. Teldat is dedicated to helping organizations build secure and reliable infrastructures that can handle the demands of the modern digital environment.